Find the best Help Desk Software
Compare Products
Showing 1 - 20 of 1027 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
SysAid
SysAid
FrontRunners 2024
SysAid empowers organizations to deliver exceptional service – automagically. A comprehensive, next-gen ITSM platform, SysAid comes ready for action with generative AI baked into every element of service management, all wrapped up...Read more about SysAid
JumpCloud Directory Platform
JumpCloud Directory Platform
JumpCloud Directory-as-a-Service is an IT Management software, which helps businesses of all sizes manage devices or workstations including Windows, MacOS, and Linux, access to IT resources, and user identities. The solution provi...Read more about JumpCloud Directory Platform
Zendesk Suite
Zendesk Suite
Zendesk is a cloud-based help desk management solution offering customizable tools to build customer service portal, knowledge base and online communities. The solution offers a customizable front-end portal, live chat features an...Read more about Zendesk Suite
Issuetrak
Issuetrak
FrontRunners 2024
Issuetrak is a flexible issue tracking software solution that can be configured to suit the needs of a variety of industries and usages, including IT Help Desk, Customer Support, Project Management, and more. Issuetrak can be dep...Read more about Issuetrak
Talk with us for a free
15-minute consultationSoftware Advice is free because vendors pay us when they receive sales opportunities.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
Meet Eric, a software expert who has helped 1,534 companies select the right product for their needs.
Talk with us for a free
15-minute consultationSoftware Advice is free because vendors pay us when they receive sales opportunities.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
Tell us more about your business and an advisor will reach out with a list of software recommendations customized for your specific needs.
STEP 1 OF 4
How many employees are in your company?
Vivantio
Vivantio
Founded in 2003, Vivantio is a leading provider of service management software for both internal- and external-facing teams. Centralize your service operations across IT, HR, GRC, Facilities, Finance, Legal and B2B Customer Suppor...Read more about Vivantio
BOSSDesk
BOSSDesk
FrontRunners 2024
BOSSDesk ITSM Help Desk Ticketing System on the Cloud and On Premise Turning ticket management into an exceptional customer experience! With rapidly increasing service requests, is your company maximizing its investment in your ...Read more about BOSSDesk
Summit
Summit
SymphonyAI Summit is an AI-powered IT service management (ITSM) suite that streamlines service and asset management across the enterprise with machine learning and workflow-based automation. As a true multi-tenant solution, Sympho...Read more about Summit
TeamSupport
TeamSupport
TeamSupport is a robust customer support solution designed to improve customer satisfaction, simplify workflows, and make agents’ lives easier. We empower teams of all sizes to consolidate channels, shorten time to resolution, col...Read more about TeamSupport
N-central
N-central
N-able N-central® is an IT management solution that enables organizations to manage and track IT devices. The solution comes with key features that include patch management, antivirus protection, backup and disaster recovery. The...Read more about N-central
Tidio
Tidio
FrontRunners 2024
Tidio Chat is a cloud-based live chat platform suitable for integration into any company’s website. It includes a customizable interface that lets companies make the live chat interface match the look and feel of existing online a...Read more about Tidio
Canfigure
Canfigure
Canfigure is a modular solution CMDB, Asset Management, Service Management, Change Management and more. You can choose the modules that you require and customize them to suit your business. Canfigure comes with all the tools nece...Read more about Canfigure
NinjaOne
NinjaOne
FrontRunners 2024
NinjaOne is a leading unified IT management software company that simplifies how IT teams work. MSPs and IT departments can automate, manage, and remediate all their device management tasks within one fast, modern, intuitive platf...Read more about NinjaOne
Syxsense
Syxsense
Syxsense is a leading Unified Security and Endpoint Management (USEM) solution that delivers real-time monitoring and intelligent automation for vulnerability management, patch management, and security remediation in a single con...Read more about Syxsense
Setyl
Setyl
Track assets and subscription renewals, improve on and off boarding processes, analyze spend and stay compliant, in one comprehensive platform. Setyl is a cloud based IT management platform that integrates across your IT landscape...Read more about Setyl
EV Service Manager
EV Service Manager
EasyVista is a help desk solution for large companies in industries including accounting, banking, agriculture, manufacturing, non-profit, food & beverage, healthcare, transportation and many more. The software is offered through ...Read more about EV Service Manager
Slack
Slack
Slack is a cloud-based project collaboration and team interaction tool designed to facilitate communication across organizations. The solution caters to various industries, including media, research, technology, education, financi...Read more about Slack
TeamViewer Remote
TeamViewer Remote
TeamViewer is an online meeting and video conferencing solution that connects any PC, mobile, and server to each other globally. The solution is available in nearly all countries and supports over 30 languages. TeamViewer is suita...Read more about TeamViewer Remote
Wix
Wix
Wix is a cloud-based landing page solution that helps users create and manage websites. The solution provides multiple templates with video backgrounds, fonts and animation. It allows users to customize the website with their own ...Read more about Wix
Microsoft SharePoint
Microsoft SharePoint
Microsoft Sharepoint is a knowledge and content management system (CMS). The product also provides collaboration tool capabilities. The solution offers typical CMS features like document and digital asset management, case and cont...Read more about Microsoft SharePoint
monday.com
monday.com
monday.com is an award-winning work and project management platform that helps teams of all sizes plan, prioritize, manage, and execute their work more effectively. The platform offers solutions for a wide range of use-cases such...Read more about monday.com
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023Service desk agents need to respond to a constant stream of end-user queries regarding IT issues, product information, and installations. And it's just as important to keep track of every issue/incident as it is to solve them.
Manually entering requests in a system, categorizing them, and creating support tickets wastes a lot of time and resources. Help desk software helps automate most of the steps in this process, allowing faster resolution of immediate needs, incidents, and technical issues users.
Help desk tools allows support agents to consolidate tickets from multiple channels (e.g., email, live chat, calls, self-service portals). Managers can access key information such as workload, incident turnaround time, and resolution rate.
Help desk software often integrates with customer service, customer relationship management, contact center, and knowledge base software to facilitate better customer service and support. This buyers guide explains what help desk software is and what to look for to find the best help desk tool for your business.
Here’s what we'll cover:
What is help desk software?
Help desk software helps businesses and support teams accept, manage, organize, automate, respond to, and report on customer questions or issues. These tools centralize information and support management to automate the complaint resolution process. Help desk systems can be used for external customer service or internal IT support within an organization.
Some customer relationship management (CRM) software offers help desk functionality. Help desk software can often integrate with CRM software or other tools to access customer data and facilitate customer service.
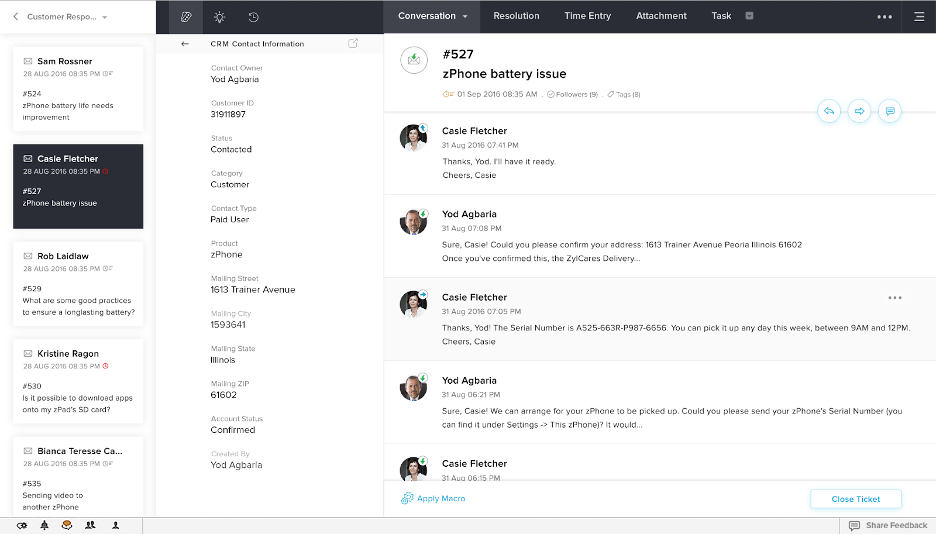
Interaction tracking in Zoho Desk software (Source)
Common features of help desk software
Facilitate virtual conferences that connect multiple people remotely over the phonCreate, store and share information, FAQs, and support articles in a central database. Employees or customers can self-navigate through the knowledge base to find answers without waiting for a support agent. | |
Ticket management | Consolidate and track all end-user issues from different sources (phone, email, chat, request forms, etc.) and convert them into tickets. |
Alerts/Escalation | Send notifications to support desk agents about ticket prioritization. |
Interaction tracking | Add notes, conversation history, and actions taken to each issue/incident. This helps service desk agents keep track of tickets, reference past issues, identify repeat incidents, and more. |
Reporting/analytics | Analyze customer support performance by tracking average response time, ticket volume, request/ticket sources, and more. |
Self-service portal | Allow end-users to answer their own questions without support agents by browsing knowledge base articles, using self-service forums, and easily contacting support to follow-up on past requests. |
Service-level agreement (SLA) management | Document an agreement between the provider and end-user that identifies services required and expected level of service. |
Workflow configuration | Change, adjust, and configure your workflow based on business needs and user-defined rules to help automate repetitive and manual tasks. |
Multi-channel communication | Give end-users the option to submit requests via multiple channels such as email, live chat, text, voice, online forms, and social media. This reduces customer wait time and speeds up the issue resolution process. |
What type of buyer are you?
Before purchasing a help desk solution, you should assess what kind of a buyer you are. Most buyers fall into two categories:
Buyers serving external customers: Buyers in this category directly serve customers and handle customer-generated queries. Help desk software for these buyers allows customer service teams to create support tickets to track customer issues and solutions.
These buyers should look for help desk tools that offer live chat, social media integration, multi-channel communication, call center management, alerts, and reporting capabilities to provide service desk agents with a holistic view of all tickets, allow them to organize tickets, and improve customer satisfaction by providing faster support.
Buyers serving employees: Internal employees often need support regarding IT, HR, and admin-related issues. Buyers in this segment need help desk software that includes internal ticketing, a knowledge base, and the ability to assign/route employee-generated tickets to relevant staff.
These buyers should invest in a help desk system that provides employee self-service options, live chat, reporting and analytics, automated routing, and email management functionalities. Ideally, these buyers should also look for features such as IT service management and incident management so staff can easily check on ticket status and progress.
Benefits of help desk software
Better customer support: Help desk software organizes communication in a central location so businesses can quickly respond to customers. Automated ticket routing and multi-channel communication capabilities can help support staff prioritize tickets and avoid duplicate tickets.
Improved productivity: Help desk software automation features reduce the amount of manual administrative and organizational tasks agents need to complete. These tools can automatically route tickets to team members who specialize in specific issues and complaints. The ability to add notes to a conversation and respond to common questions with saved replies can also help boost productivity.
Better decision-making: The reporting capabilities of help desk software provide key insights regarding ticket resolution times, customer satisfaction, employee productivity, and customer experience so businesses can understand how things are working overall and make decisions to optimize.
Key considerations
Easy-to-use interface: Choose a tool that has a shorter learning curve for employees and an intuitive interface. Look for help desk software that provides a free trial, demo sessions, and training videos so employees can get up-to-speed as quickly as possible.
Scalability: As your team continues to grow, so will your needs. Finding a solution that grows with your business is important. Look for a cloud-based solution or web help desk platform that can support a large volume of customers and adapt to different use cases and issues.
Customer expectations: Before buying a help desk tool, it is important to know how your customers would prefer to interact with you? Do they prefer self service tools, emails, chat services, or a mobile-friendly knowledge base? Make sure to invest in a help desk platform, after considering your customers’ satisfaction and dissatisfaction.
Market trends to understand
Cognitive automation of help desk software: Advancements in machine learning technology have prompted help desk service providers to add cognitive automation to their tools. This technology can help extract key phrases from employee or customer requests, categorize them, create support tickets, and route them to specific groups. Help desk providers that integrate cognitive automation into their software can help businesses save more time and money as employees have even fewer manual tasks to complete.
Note: The application selected in this article is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been obtained from sources believed to be reliable at the time of publication.